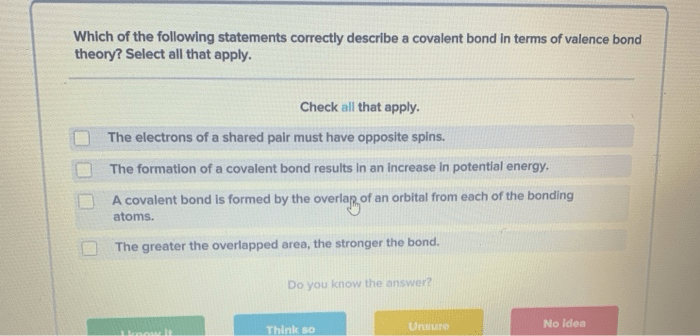
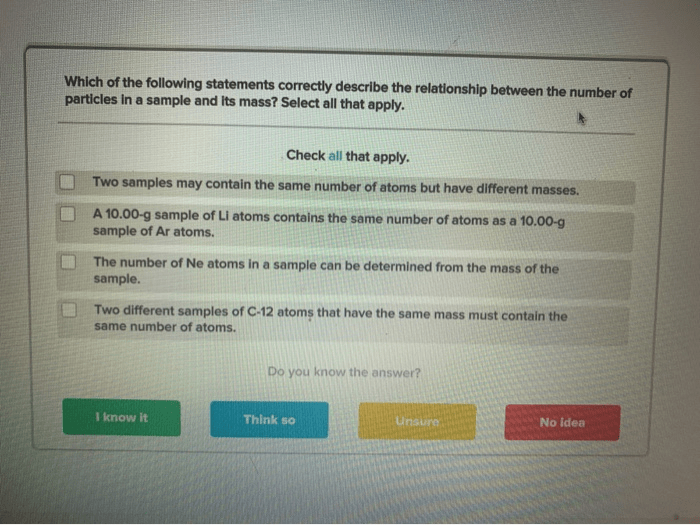
Select the statements that correctly describe a buffer: In the realm of computer science, buffers play a pivotal role in data management and processing. They serve as temporary storage areas, facilitating seamless data transfer between different components of a system.
This article delves into the intricacies of buffers, exploring their types, management techniques, security considerations, and practical applications.
Buffers are ubiquitous in computing, from operating systems and databases to networking and multimedia applications. Their efficient utilization is crucial for maintaining system stability, performance, and security.
Buffer in Computer Science
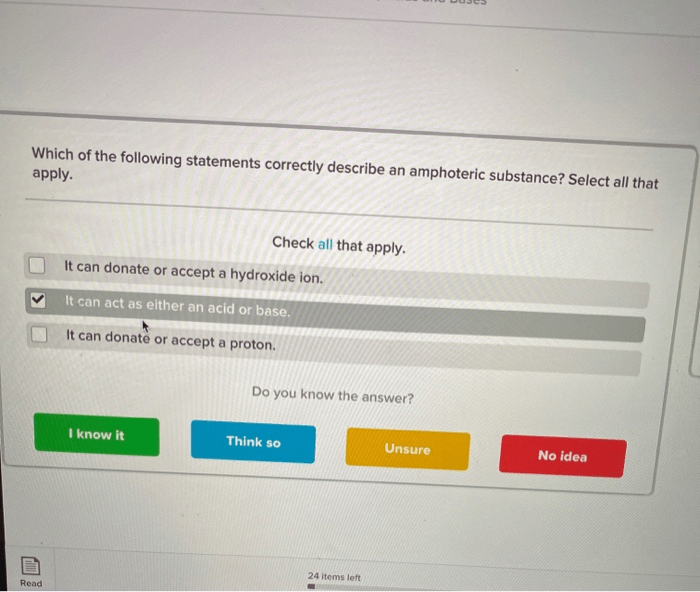
In computer science, a buffer is a temporary storage area used to hold data while it is being transferred between two devices or programs.
Buffers are commonly used to improve the performance of computer systems by reducing the amount of time spent waiting for data to be transferred.
Types of Buffers
- Input buffer:Stores data received from an input device, such as a keyboard or mouse.
- Output buffer:Stores data to be sent to an output device, such as a printer or display.
- Circular buffer:A special type of buffer that allows data to be written and read at different positions, without overwriting existing data.
- Double buffer:A pair of buffers that are used to avoid tearing or flickering during graphics rendering.
Buffer Management
Effective buffer management involves allocating and deallocating buffers efficiently to avoid memory leaks and performance issues.
Buffer allocation involves determining the appropriate size and location for the buffer, while buffer deallocation involves releasing the memory occupied by the buffer when it is no longer needed.
Buffer Overflow
Buffer overflow occurs when data is written to a buffer beyond its capacity, overwriting adjacent memory locations.
Buffer overflows can lead to security vulnerabilities, such as memory corruption and code execution.
Buffer Underflow, Select the statements that correctly describe a buffer
Buffer underflow occurs when data is read from a buffer that has not been filled to its capacity.
Buffer underflows can lead to incorrect or incomplete data being processed.
Buffer Security
Buffer security is critical to prevent buffer overflow and underflow attacks.
Techniques for preventing buffer overflow include input validation, boundary checking, and using secure coding practices.
Buffer Optimization
Buffer optimization techniques aim to minimize buffer overhead and improve performance.
This involves using appropriate buffer sizes, avoiding unnecessary buffer copies, and employing efficient buffer management algorithms.
Buffer Applications
Buffers are widely used in various applications, including:
- Operating systems: To manage input and output operations.
- Networking: To store data during network communication.
- Multimedia: To buffer audio and video streams.
- Databases: To cache frequently accessed data.
Quick FAQs: Select The Statements That Correctly Describe A Buffer
What is the primary function of a buffer?
A buffer’s primary function is to act as a temporary storage area for data, facilitating seamless transfer between different components of a system.
What are the potential consequences of buffer overflow?
Buffer overflow can lead to system crashes, data corruption, and security vulnerabilities that can be exploited by malicious actors.
How can buffer security be enhanced?
Buffer security can be enhanced through techniques such as boundary checking, input validation, and the use of secure programming practices.